Has anyone taken this Cisco 642-737 dumps. The “Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0” certification 642-737 dumps exam verifies that the candidate possesses the deep knowledge required in the area of CCNP Wireless. Latest Cisco 642-737 dumps IAUWS study guide for cisco certification latest version pdf&vce video training. This certificate proves that the candidate has an advanced understanding to secure the wireless network from security threats via appropriate security policies and best practices, to properly implement security standards, and to properly configure wireless security components and is able to apply these skills practically and provide guidance in IAUWS Implementing Advanced Cisco Unified Wireless Security course. Our exam never feels satisfactory about what he achieved. Instead, we keeps on trying to provide candidates with the latest and most accurate certifications. It is associated with a CCNP Wireless certification. Professionals in our collected 207 Q&As questions and answers for candidates’ https://www.pass4itsure.com/642-737.html dumps exams preparation.
Kill your exam with Cisco 642-737 dumps real questions(25-44)
QUESTION 25
Which attribute on the Cisco WLC v7.0 does RADIUS IETF attribute “Tunnel-Private-Group ID” assign?
A. ACL
B. DSCP
C. QoS
D. VLAN
642-737 exam Correct Answer: D
QUESTION 26
How do you configure the Cisco Secure ACS v4.2 and Cisco WLC v7.0 to provide the most flexibility for the management of authorized access on the WLC?
A. Local management user defined on the WLC
B. The WLC configured for RADIUS and the Cisco Secure ACS configured for RADIUS (Cisco Airespace)
C. The WLC configured for RADIUS and the Cisco Secure ACS configured for RADIUS (IETF)
D. The WLC configured for TACACS+ and the Cisco Secure ACS configured for TACACS+ (Cisco Airespace)
E. The WLC configured for TACACS+ and the Cisco Secure ACS configured for TACACS+ (Cisco IOS)
Correct Answer: E
QUESTION 27
The Cisco WLC v7.0 is configured for external 802.1X and EAP by using the WPA2 association of wireless clients when using the Cisco Secure ACS v4.2. Which two items are required in the Cisco Secure ACS network configuration to enable correct AAA? (Choose two.)
A. AP IP address
B. WLC virtual IP address
C. WLC management IP address
D. WLC AP management IP address
E. hostname matching the WLC case-sensitive name
F. authentication using RADIUS
G. authentication using TACACS+
642-737 dumps Correct Answer: CF
QUESTION 28
The Cisco WLC v7.0 is configured for external authentication of the management access to the WLC itself using the Cisco Secure ACS v4.2. The management user is limited to read access for all menu options except for full read/write access to the WLAN menu options. Which two items are required in the Cisco Secure ACS network configuration to enable correct AAA? (Choose two.)
A. AP IP address
B. WLC virtual IP address
C. WLC management IP address
D. WLC AP management IP address
E. hostname matching the WLC case-sensitive name
F. authentication using RADIUS
G. authentication using TACACS+
Correct Answer: CG
QUESTION 29
Configuring the Cisco Secure ACS with a self-signed certificate supports which requirement?
A. when no user certificate is required
B. when a CA-signed certificate is required for the user
C. when a self-signed certificate Class 4 is required for the user
D. when a self-signed certificate Class 0 is required for the user
642-737 pdf Correct Answer: A
QUESTION 30
When implementing certificates through the use of a CA, how is the certificate of client A validated by client B when received?
A. verifying the client A certificate using the client A private key
B. verifying the client A certificate using the client A public key
C. verifying the client A certificate using the client B private key
D. verifying the client A certificate using the client B public key
E. verifying the client A certificate using the CA private key
F. verifying the client A certificate using the CA public key
Correct Answer: F
QUESTION 31
Refer to the exhibit.
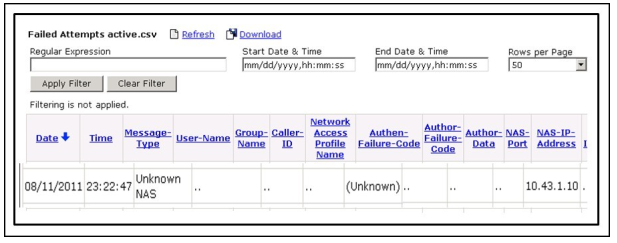
What does this Cisco Secure ACS v4.2 log indicate?
A. The WLC is not configured as a client in the Cisco Secure ACS.
B. The WLC is not configured as a server in the Cisco Secure ACS.
C. Incorrect authentication exists between the WLC and Cisco Secure ACS.
D. The wireless client is not configured as a client in the Cisco Secure ACS.
E. Incorrect authentication exists between the wireless client and Cisco Secure ACS.
642-737 vce Correct Answer: A
QUESTION 32
Authentication is failing between a client and the RADIUS server. Which WLC troubleshooting command set might be useful to assist in troubleshooting the issue?
A. show local-auth
B. debug ldap
C. debug aaa local-auth
D. debug dot1X event
Correct Answer: D
QUESTION 33 Frank wants to know why users on the corporate network cannot receive multicast transmissions from the Internet. An NGX Security Gateway protects the corporate network from the Internet. Which of the following is a possible cause for the connection problem?
A.NGX does not support multicast routing protocols and streaming media through the Security Gateway.
B.Frank did not install the necessary multicast license with SmartUpdate, when he upgraded to NGX.
C.The Multicast Rule is below the Stealth Rule. NGX can only pass multicast traffic, if the Multicast Rule is above the Stealth Rule.
D.Multicast restrictions are not configured properly on the corporate internal network interface properties of the Security Gateway object.
E.Anti-spoofing is enabled. NGX cannot pass multicast traffic, if anti-spoofing is enabled.
642-737 exam Answer:D
QUESTION 32.In NGX, what happens if a Distinguished Name (DN) is NOT found in LDAP?
A.NGX takes the common-name value from the Certificate subject, and searches the LDAP account unit for a matching user id.
B.NGX searches the internal database for the username.
C.The Security Gateway uses the subject of the Certificate as the DN for the initial lookup.
D.If the first request fails or if branches do not match, NGX tries to map the identity to the user id attribute.
E.When users authenticate with valid Certificates, the Security Gateway tries to map the identities with users registered in the external LDAP user database.
Answer:B
QUESTION 33.Gary is a Security Administrator in a small company. He needs to determine if the company’s Web servers are accessed for an excessive number of times from the same host. How would he configure this setting in SmartDefense?
A.Successive multiple connections
B.HTTP protocol inspection
C.Successive alerts
D.General HTTP worm catcher
E.Successive DoS attacks
642-737 dumps Answer:A
QUESTION 34.In SmartDashboard, you configure 45 MB as the required free hard-disk space to accommodate logs. What can you do to keep old log files, when free space falls below 45 MB?
A.Define a secondary SmartCenter Server as a log server, to transfer the old logs.
B.Configure a script to archive old logs to another directory, before old log files are deleted.
C.Do nothing. Old logs are deleted, until free space is restored.
D.Use the fwm logexport command to export the old log files to other location.
E.Do nothing. The SmartCenter Server archives old logs to another directory.
Answer:B
QUESTION 35.Brianna has three servers located in a DMZ, using private IP addresses. She wants internal users from 10.10.10.x to access the DMZ servers by public IP addresses. Internal_net 10.10.10.x is configured for Hide NAT behind the Security Gateway’s external interface. What is the best configuration for 10.10.10.x users to access the DMZ servers, using the DMZ servers’ public IP addresses?
A.Configure automatic Static NAT rules for the DMZ servers.
B.Configure manual Static NAT rules to translate the DMZ servers, when connecting to the Internet.
C.Configure manual static NAT rules to translate the DMZ servers, when the source is the internal network 10.10.10.x.
D.Configure Hide NAT for the DMZ network behind the DMZ interface of the Security Gateway, when connecting to internal network 10.10.10.x.
E.Configure Hide NAT for 10.10.10.x behind DMZ’s interface, when trying to access DMZ servers.
642-737 pdf Answer:C
QUESTION 36.You are setting up a Virtual Private Network, and must select an encryption scheme. Network performance is a critical issue – even more so than the security of the packet. Which encryption scheme would you select?
A.In-place encryption
B.Tunneling mode encryption
C.Either one will work without compromising performance
Answer:A
QUESTION 37.Larry is the Security Administrator for a software-development company. To isolate the corporate network from the developers’ network, Larry installs an internal Security Gateway. Larry wants to optimize the performance of this Gateway. Which of the following actions is most likely to improve the Gateway’s performance?
A.Remove unused Security Policies from Policy Packages.
B.Clear all Global Properties check boxes, and use explicit rules.
C.Use groups within groups in the manual NAT Rule Base.
D.Put the least-used rules at the top of the Rule Base.
E.Use domain objects in rules, where possible.
642-737 vce Answer:A
QUESTION 38.If a digital signature is used to achieve both data-integrity checking and verification of sender, digital signatures are only used when implementing:
A.A symmetric encryption algorithm.
B.CBL-DES.
C.ESP.
D.An asymmetric encryption algorithm.
E.Triple DES.
Answer:D
QUESTION 39.Ellen is performing penetration tests against SmartDefense for her Web server farm. She needs to verify that the Web servers are secure against traffic hijacks. She has selected the “Products > Web Server” box on each of the node objects. What other settings would be appropriate? Ellen:
A.needs to configure TCP defenses such as “Small PMTU” size.
B.should enable all settings in Web Intelligence.
C.needs to create resource objects for the web farm servers and configure rules for the web farm.
D.must activate the Cross-Site Scripting property.
E.should also enable the Web intelligence > SQL injection setting.
642-737 exam Answer:D
QUESTION 40.Which of the following commands is used to restore NGX configuration information?
A.cpconfig
B.cpinfo -i
C.restore
D.fwm dbimport
E.upgrade_import
Answer:E
QUESTION 41.When you change an implicit rule’s order from “last” to “first” in Global Properties, how do you make the change effective?
A.Close SmartDashboard, and reopen it.
B.Select install database from the Policy menu.
C.Select save from the file menu.
D.Reinstall the Security Policy.
E.Run fw fetch from the Security Gateway.
642-737 dumps Answer:D
QUESTION 42.Which NGX logs can you configure to send to DShield.org?
A.Account and alert logs
B.SNMP and account logs
C.Active and alert logs
D.Audit and alert logs
E.Alert and user-defined alert logs
Answer:E
QUESTION 43.How do you block some seldom-used FTP commands, such as CWD, and FIND from passing through the Gateway?
A.Use FTP Security Server settings in SmartDefense.
B.Use an FTP resource object.
C.Configure the restricted FTP commands in the Security Servers screen of the Global properties.
D.Enable FTP Bounce checking in SmartDefense.
E.Add the restricted commands to the aftpd.conf file in the SmartCenter Server.
642-737 pdf Answer:A
QUESTION 44.Your users are defined in a Windows 2000 Active Directory server. You must add LDAP users to a Client Authentication rule. Which kind of user group do you need in the Client Authentication rule in NGX?
A.All Users
B.A group with generic* user
C.External-user group
D.LDAP account-unit group
E.LDAP group
Answer:E

See What Our Customers Are Saying:
In high-technology enterprises, Cisco certification is like a pass. We at Pass4itsure are committed to our customer’s success.Our Cisco 642-737 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world. For non computer majors, if switching to Cisco industry without professional diploma, Computer Technology Industry Association Certification and other certifications become important capability proof.
Here you can download free practice tests 642-737 dumps: Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0. The Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0 (642-737 IAUWS) exam is a 90-minute, 50–60 question assessment that is associated with the associated with the CCNP Wireless certification, which covers all objectives of (Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0). Pass4itsure https://www.pass4itsure.com/642-737.html dumps free exam is the exam code of Computer Technology Industry Association exam.The material covers every field the exam required.
[Up To Dated -2018 Cisco 642-737 Dumps From Google Drive]: https://drive.google.com/open?id=1Mt1tw_DnjumL9gPlku7ChvdbfvwmttME
[Up To Dated -2018 Cisco 642-883 Dumps From Google Drive]: https://drive.google.com/open?id=1cHxworTp2CNJ9BobLBGoggxUdcs3CmpZ
But when facing various Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0 Cisco exams and strong promotions, many people find it is hard to figure out which one is better. Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure Cisco 642-737 Dumps Exam Guide, Buy Latest Cisco 642-737 Dumps Exams Latest Version PDF&VCE, We Help You Pass Implementing Advanced Cisco Unified Wireless Security (IAUWS) v2.0.
