
Yes, absolutely!
Cisco 200-201 dumps have two practice methods, PDF and VCE!
Search data from Google, Youtube, Reddit, and Meta… reveals that a large percentage of candidates are looking for Cisco 200-201 exam practice materials! their first step through various learning styles
Help them learn the Cisco 200-201 exam content by themselves, the second step is to get the latest Cisco 200-201 dumps practice materials before the exam to help them easily pass the Cisco 200-201 certification exam.
PS. This is the safest way to learn! It is also the best solution to pass the exam successfully!
Next, provide candidates with a copy of the latest Cisco 200-201 dumps practice material for free:
Pass4itsure 200-201 dumps exam materials shared online:
| From | Number of exam questions | Type | Associated certification |
| Pass4itsure | 15/264 | Free | Cisco Certified CyberOps Associate |
Question 1:
What is the difference between a threat and a risk?
A. Threat represents a potential danger that could take advantage of a weakness in a system
B. Risk represents the known and identified loss or danger in the system
C. Risk represents the nonintentional interaction with uncertainty in the system
D. Threat represents a state of being exposed to an attack or a compromise, either physically or logically.
Correct Answer: A
A threat is any potential danger to an asset. If a vulnerability exists but has not yet been exploited–or, more importantly, it is not yet publicly known–the threat is latent and not yet realized.
Question 2:
What is the difference between statistical detection and rule-based detection models?
A. Rule-based detection involves the collection of data in relation to the behavior of legitimate users over a period of time
B. Statistical detection defines legitimate data of users over a period of time and rule-based detection defines it on an IF/THEN basis
C. Statistical detection involves the evaluation of an object on its intended actions before it executes that behavior
D. Rule-based detection defines legitimate data of users over a period of time and statistical detection defines it on an IF/THEN basis
Correct Answer: B
Question 3:
DRAG DROP
Drag and drop the security concept from the left onto the example of that concept on the right.
Select and Place:
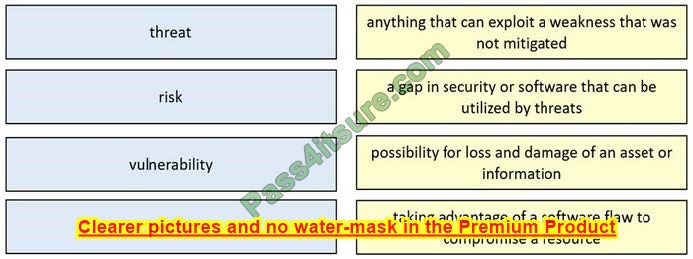
Correct Answer:
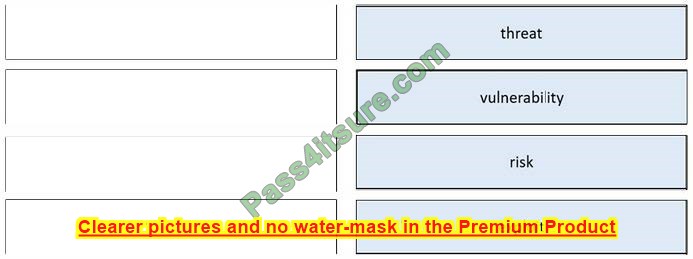
Question 4:
What is the difference between discretionary access control (DAC) and role-based access control (RBAC)?
A. DAC requires explicit authorization for a given user on a given object, and RBAC requires specific conditions.
B. RBAC access is granted when a user meets specific conditions, and in DAC, permissions are applied on user and group levels.
C. RBAC is an extended version of DAC where you can add an extra level of authorization based on time.
D. DAC administrators pass privileges to users and groups, and in RBAC, permissions are applied to specific groups
Correct Answer: A
Question 5:
Which security technology allows only a set of pre-approved applications to run on a system?
A. application-level blacklisting
B. host-based IPS
C. application-level whitelisting
D. antivirus
Correct Answer: C
Question 6:
During which phase of the forensic process is data that is related to a specific event labeled and recorded to preserve its integrity?
A. examination
B. investigation
C. collection
D. Reporting
Correct Answer: C
Question 7:
Which category relates to improper use or disclosure of PII data?
A. legal
B. compliance
C. regulated
D. contractual
Correct Answer: C
Question 8:
How does an attack surface differ from an attack vector?
A. An attack vector recognizes the potential outcomes of an attack, and the attack surface is choosing a method of attack.
B. An attack surface identifies vulnerable parts for an attack, and an attack vector specifies which attacks are feasible to those parts.
C. An attack surface mitigates external vulnerabilities, and an attack vector identifies mitigation techniques and possible workarounds.
D. An attack vector matches components that can be exploited, and an attack surface classifies the potential path for exploitation
Correct Answer: B
Question 9:
Which attack method intercepts traffic on a switched network?
A. denial of service
B. ARP cache poisoning
C. DHCP snooping
D. command and control
Correct Answer: B
An ARP-based MITM attack is achieved when an attacker poisons the ARP cache of two devices with the MAC address of the attacker\’s network interface card (NIC).
Once the ARP caches have been successfully poisoned, each victim device sends all its packets to the attacker when communicating with the other device and puts the attacker in the middle of the communications path between the two victim devices.
It allows an attacker to easily monitor all communication between victim devices. The intent is to intercept and view the information being passed between the two victim devices and potentially introduce sessions and traffic between the two victim devices
Question 10:
Refer to the exhibit.

An analyst received this alert from the Cisco ASA device, and numerous activity logs were produced. How should this type of evidence be categorized?
A. indirect
B. circumstantial
C. corroborative
D. best
Correct Answer: C
Indirect=circumstantail so there is no possibility to match A or B (only one answer is needed in this question).
For sure it\’s not the BEST evidence – this FW data inform only of DROPPED traffic. If smth happened inside the network, presented evidence could be used to support other evidence or make our narrative stronger but alone it means nothing.
Question 11:
Refer to the exhibit.
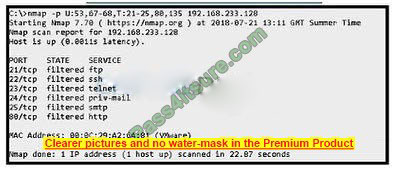
An attacker scanned the server using Nmap. What did the attacker obtain from this scan?
A. Identified a firewall device preventing the pert state from being returned.
B. Identified open SMB ports on the server
C. Gathered information on processes running on the server
D. Gathered a list of Active Directory users
Correct Answer: C
Question 12:
Refer to the exhibit.
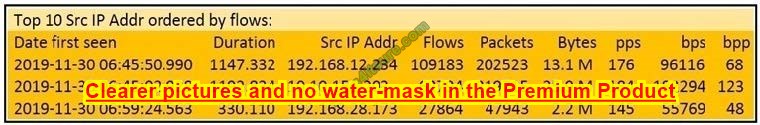
What information is depicted?
A. IIS data
B. NetFlow data
C. network discovery event
D. IPS event data
Correct Answer: B
Question 13:
What is the virtual address space for a Windows process?
A. physical location of an object in memory
B. set of pages that reside in the physical memory
C. system-level memory protection feature built into the operating system
D. set of virtual memory addresses that can be used
Correct Answer: D
Question 14:
Refer to the exhibit.
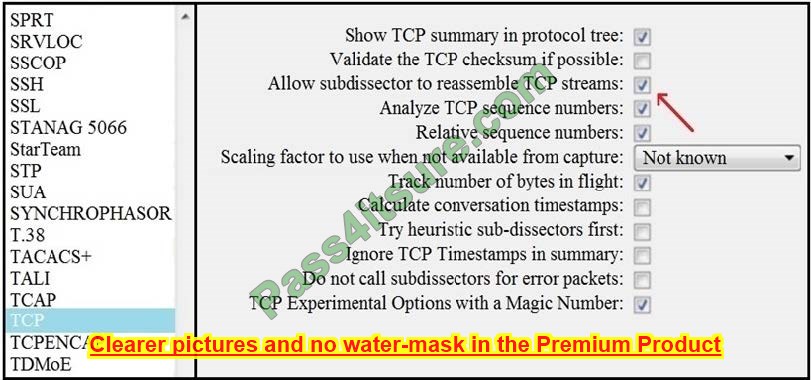
What is the expected result when the “Allow sub dissector to reassemble TCP streams” feature is enabled?
A. insert TCP sub dissectors
B. extract a file from a packet capture
C. disable TCP streams
D. unfragmented TCP
Correct Answer: D
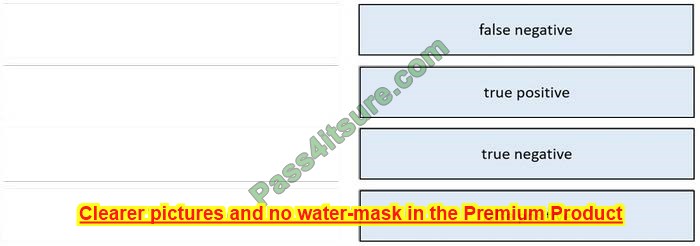
Question 15:
DRAG DROP
Drag and drop the event term from the left onto the description on the right.
Select and Place:

Correct Answer:
…
According to Cisco statistics, 4 million people have entered this industry during Cisco’s 30 years of development! It is expected to reach 10 million in the next 30 years! So will you be one of them?
Pass4itsure recommends the best learning plan for the Cisco 200-201 exam to help you become a member of Cisco. You only need two steps: The first step is to complete the study of Cisco 200-201 exam knowledge, which is helpful for your career planning!
In the second step, use the Cisco 200-201 dumps practice material to help you prepare before the exam, because it can guarantee you 100% success in passing the exam.
