
Pass4itSure has launched a new version of CompTIA CS0-003 dumps to help you study, with the latest updates of 425+ new exam questions!
Download the new CS0-003 dumps https://www.pass4itsure.com/cs0-003.html Select Tool PDF or VCE to prepare for the CompTIA CySA+ CS0-003 exam easily.
Valid and new CS0-003 dumps online exam questions sharing
You google “CS0-003 online exam questions” and there are many but very few that are valid and up-to-date. Here are the new CS0-003 online exam questions, which are guaranteed valid.
From where: Pass4itSure
How many questions: 15/452
What are the advantages: There are not only correct answers to questions but also explanations and links to relevant materials
Related: CompTIA CySA+, CompTIA
Free or charged: free
Question 1:
A digital forensics investigator works from duplicate images to preserve the integrity of the original evidence. Which of the following types of media are MOST volatile and should be preserved? (Choose two.)
A. Memory cache
B. Registry file
C. SSD storage
D. Temporary filesystems
E. Packet decoding
F. Swap volume
Correct Answer: AD
Question 2:
Which of the following weaknesses associated with common SCADA systems are the MOST critical for organizations to address architecturally within their networks? (Choose two.)
A. Boot processes that are neither measured nor attested
B. Legacy and unmatchable systems software
C. Unnecessary open ports and protocols
D. No OS kernel mandatory access controls
E. Unauthenticated commands
F. Insecure filesystem permissions
Correct Answer: BF
Question 3:
During a company\’s most recent incident, a vulnerability in custom software was exploited on an externally facing server by an APT. The lessons-learned report noted the following:
The development team used a new software language that was not supported by the security team\’s automated assessment tools.
During the deployment, the security assessment team was unfamiliar with the new language and struggled to evaluate the software during advanced testing. Therefore, the vulnerability was not detected. The current IPS did not have effective signatures and policies in place to detect and prevent runtime attacks on the new application.
To allow this new technology to be deployed securely going forward, which of the following will BEST address these findings? (Choose two.)
A. Train the security assessment team to evaluate the new language and verify that best practices for secure coding have been followed
B. Work with the automated assessment tool vendor to add support for the new language so these vulnerabilities are discovered automatically
C. Contact the human resources department to hire new security team members who are already familiar with the new language
D. Run the software on isolated systems so that when they are compromised, the attacker cannot pivot to adjacent systems
E. Instruct only the development team to document the remediation steps for this vulnerability
F. Outsource development and hosting of the applications in the new language to a third-party vendor so the risk is transferred to that provider
Correct Answer: AB
Question 4:
A security operations manager wants some recommendations for improving security monitoring. The security team currently uses past events to create an IoC list for monitoring. Which of the following is the best suggestion for improving monitoring capabilities?
A. Update the IPS and IDS with the latest rule sets from the provider.
B. Create an automated script to update the IPS and IDS rule sets.
C. Use an automated subscription to select threat feeds for IDS.
D. Implement an automated malware solution on the IPS.
Correct Answer: C
Question 5:
While reviewing a vulnerability assessment, an analyst notices the following issue is identified in the report:
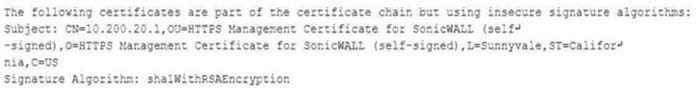
this finding, which of the following would be most appropriate for the analyst to recommend to the network engineer?
A. Reconfigure the device to support only connections leveraging TLSv1.2.
B. Obtain a new self-signed certificate and select AES as the hashing algorithm.
C. Replace the existing certificate with a certificate that uses only MD5 for signing.
D. Use only signed certificates with cryptographically secure certificate sources.
Correct Answer: D
Question 6:
A recent penetration test discovered that several employees were enticed to assist attackers by visiting specific websites and running downloaded files when prompted by phone calls. Which of the following would best address this issue?
A. Increasing training and awareness for all staff
B. Ensuring that malicious websites cannot be visited
C. Blocking all scripts downloaded from the internet
D. Disabling all staff member’s ability to run downloaded applications
Correct Answer: A
Question 7:
Which of the following activities is designed to handle a control failure that leads to a breach?
A. Risk assessment
B. Incident management
C. Root cause analysis
D. Vulnerability management
Correct Answer: B
Incident management is a process that aims to handle a control failure that leads to a breach by restoring normal operations as quickly as possible and minimizing the impact and damage of the incident. Incident management involves activities such as identifying, analyzing, containing, eradicating, recovering, and learning from security incidents. Risk assessment, root cause analysis, and vulnerability management are other processes related to security management, but they are not designed to handle a control failure that leads to a breach.
Reference: https://www.sans.org/reading-room/whitepapers/incident/incident-handlers-handbook-33901
Question 8:
Which of the following best describes the reporting metric that should be utilized when measuring the degree to which a system, application, or user base is affected by an uptime availability outage?
A. Timeline
B. Evidence
C. Impact
D. Scope
Correct Answer: C
The impact metric is the best way to measure the degree to which a system, application, or user base is affected by an uptime availability outage. The impact metric quantifies the consequences of the outage in terms of lost revenue, productivity, reputation, customer satisfaction, or other relevant factors. The impact metric can help prioritize the recovery efforts and justify the resources needed to restore the service.
The other options are not the best ways to measure the degree to which a system, application, or user base is affected by an uptime availability outage. The timeline metric (A) measures the duration and frequency of the outage, but not its effects. The evidence metric (B) measures the sources and types of data that can be used to investigate and analyze the outage, but not its effects. The scope metric (D) measures the extent and severity of the outage, but not its effects.
Question 9:
Which of the following ICS network protocols has no inherent security functions on TCP port 502?
A. CIP
B. DHCP
C. SSH
D. Modbus
Correct Answer: D
Modbus is an industrial control system (ICS) network protocol that is used for communication between devices such as sensors, controllers, actuators, and monitors. Modbus has no inherent security functions on TCP port 502, which is the default port for Modbus TCP/IP communication.
Modbus does not provide any encryption, authentication, or integrity protection for the data transmitted over the network, making it vulnerable to various attacks such as replay, modification, spoofing, or denial of service.
Question 10:
A security analyst is revising a company\’s MFA policy to prohibit the use of short message service (SMS) tokens. The Chief Information Officer has questioned this decision and asked for justification. Which of the following should the analyst provide as justification for the new policy?
A. SMS relies on untrusted, third-party carrier networks.
B. SMS tokens are limited to eight numerical characters.
C. SMS is not supported on all handheld devices in use.
D. SMS is a cleartext protocol and does not support encryption.
Correct Answer: D
Question 11:
During the log analysis phase, the following suspicious command is detected
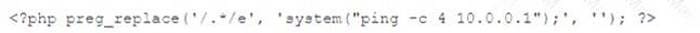
Which of the following is being attempted?
A. Buffer overflow
B. RCE
C. ICMP tunneling
D. Smurf attack
Correct Answer: B
RCE stands for remote code execution, which is a type of attack that allows an attacker to execute arbitrary commands on a target system. The suspicious command in question is an example of RCE, as it tries to download and execute a malicious file from a remote server using the wget and chmod commands.
A buffer overflow is a type of vulnerability that occurs when a program writes more data to a memory buffer than it can hold, potentially overwriting other memory locations and corrupting the program\’s execution. ICMP tunneling is a technique that uses ICMP packets to encapsulate and transmit data that would normally be blocked by firewalls or filters.
A smurf attack is a type of DDoS attack that floods a network with ICMP echo requests, causing all devices on the network to reply and generate a large amount of traffic. Verified References: What Is Buffer Overflow? Attacks, Types, and Vulnerabilities – Fortinet1, What Is a Smurf Attack? Smurf DDoS Attack | Fortinet2, exploit – Interpreting CVE ratings: Buffer Overflow vs. Denial of …3
Question 12:
A security analyst needs to ensure that systems across the organization are protected based on the sensitivity of the content each system hosts. The analyst is working with the respective system owners to help determine the best methodology that seeks to promote confidentiality, availability, and integrity of the data being hosted. Which of the following should the security analyst perform first to categorize and prioritize the respective systems?
A. Interview the users who access these systems.
B. Scan the systems to see which vulnerabilities currently exist.
C. Configure alerts for vendor-specific zero-day exploits.
D. Determine the asset value of each system.
Correct Answer: D
Determining the asset value of each system is the best action to perform first, as it helps to categorize and prioritize the systems based on the sensitivity of the data they host. The asset value is a measure of how important a system is to the organization, in terms of its financial, operational, or reputational impact.
The asset value can help the security analyst to assign a risk level and a protection level to each system, and to allocate resources accordingly. The other actions are not as effective as determining the asset value, as they do not directly address the goal of promoting confidentiality, availability, and integrity of the data.
Interviewing the users who access these systems may provide some insight into how the systems are used and what data they contain, but it may not reflect the actual value or sensitivity of the data from an organizational perspective. Scanning the systems to see which vulnerabilities currently exist may help to identify and remediate some security issues, but it does not help to categorize or prioritize the systems based on their data sensitivity.
Configuring alerts for vendor-specific zero-day exploits may help to detect and respond to some emerging threats, but it does not help to protect the systems based on their data sensitivity.
Question 13:
A large company would like a security analyst to recommend a solution that will allow only company laptops to connect to the corporate network. Which of the following technologies should the analyst recommend?
A. UEBA
B. DLP
C. NAC
D. EDR
Correct Answer: C
Question 14:
A. Any discovered vulnerabilities will not be remediated.
B. An outage of machinery would cost the organization money.
C. Support will not be available for the critical machinery.
D. There are no compensating controls in place for the OS.
Correct Answer: A
As the OS that controls the business-critical machinery is approaching its end-of-life date, it means that the OS will no longer receive updates and security patches from the vendor. This leaves the OS and the machinery susceptible to
potential security breaches and attacks that could exploit these unpatched vulnerabilities.
Question 15:
A security analyst is trying to identify anomalies in the network routing. Which of the following functions can the analyst use on a shell script to achieve the objective most accurately?
A. function x() { info=$(GeoIP lookup $1) and echo “$1 | $info” }
B. function x() { info=$(ping -c 1 $””o “$1 | $info” }
C. function x() { info=$(dig $(dig -x $1 | grep PTR | tail -n 1 | awk -F “.in-a” \’).origin.asn.cymru.com TXT +short) and and echo “$1 | $info” }
D. function x() { info=$(traceroute””$1 | $info” }
Correct Answer: C
The function that can be used on a shell script to identify anomalies on the network routing most accurately is: function x() { info=(dig(dig -x $1 | grep PTR | tail -n 1 | awk” ” ” } This function takes an IP address as an argument and performs two DNS lookups using the dig command. The first lookup uses the -x option to perform a reverse DNS lookup and get the hostname associated with the IP address.
The second lookup uses the origin.asn.cymru.com domain to get the autonomous system number (ASN) and other information related to the IP address. The function then prints the IP address and the ASN information, which can help identify any routing anomalies or inconsistencies
Reject invalid sharing! The CS0-003 exam practice questions shared here are all valid.
Share another wave of new CS0-003 exam study resources:
- CompTIA Cybersecurity Analyst (CySA+)
- CompTIA CySA+ CS0-003 Certification Study Guide
- CertMaster Practice for CySA+ Training
- Instructor-Led Training
- Interactive Labs with CertMaster Labs
- CompTIA Cybersecurity Analyst (CySA+) Cert Guide
- CompTIA Cybersecurity Analyst (CySA+) CS0-002 Cert Guide Pearson uCertify Course and Labs Access Code Card
- CompTIA CySA+ Study Guide: Exam CS0-002
New CS0-003 dumps get https://www.pass4itsure.com/cs0-003.html (New more than 425 New Exam Questions) Use the tool PDF or VCE to study and pass the CS0-003 exam easily.
I am waiting for your good news.
