
What’s new in the Cisco 400-251 dumps exam? The CCIE Security Written Exam (v5.0) (400-251 CCIE Security) exam is a 120 minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Security certification. Latest Cisco CCIE Security 400-251 dumps certification exam are based on the real exam video practice questions. “CCIE Security Written Exam (v5.0)” is the exam name of Pass4itsure Cisco 400-251 dumps test which designed to help candidates prepare for and pass the Cisco 400-251 exam. Then you can try the Pass4itsure Cisco CCIE Security 400-251 CCIE Security practice questions. Pass4itsure can escort you to pass the IT exam. Cisco CCIE Security https://www.pass4itsure.com/400-251.html dumps CCIE Security practice questions of Pass4itsure are currently the most popular materials on the internet.
[Up To Dated -2018 Cisco 400-251 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWN3NKQ2VvYmxCMDg
[Up To Dated -2018 Cisco 200-310 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWajNRNzNfaDllX3M
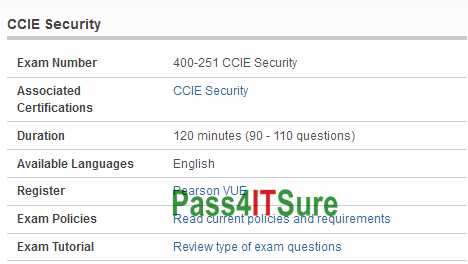
Kill your exam with Cisco 400-251 dumps real questions(11-34)
QUESTION: 11. You have just become the senior security professional in your office. After you have taken a complete inventory of the network and resources, you begin to work on planning for a successful security implementation in the network. You are aware of the many tools provided for securing Windows 2003 machines in your network. What is the function of Secedit.exe?
A. This tool is used to set the NTFS security permissions on objects in the domain.
B. This tool is used to create an initial security database for the domain.
C. This tool is used to analyze a large number of computers in a domain-based infrastructure.
D. This tool provides an analysis of the local system NTFS security.
E. This tool provides a single point of management where security options can be applied to a local computer or can be imported to a GPO.
400-251 exam Answer: C
QUESTION: 12. To increase the security of your network and systems, it has been decided that EFS will be implemented in the appropriate situations. Two users are working on a common file, and often email this file back and forth between each other. Is this a situation where the use of EFS will create effective security, and why (or why not)?
A. No, the security will remain the same since both users will share the same key for encryption.
B. Yes, since the file will be using two keys for encryption the security will increase.
C. No, the security will remain the same since both users will share the same key for decryption.
D. Yes, since the file will be using two keys for decryption the security will increase.
E. No, EFS cannot be used for files that are shared between users.
Answer: E
QUESTION: 13. Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
A. Windows 2000 Ping Request
B. Windows NT 4.0 Ping Request
C. Linux Ping Request
D. Linux Ping Response
E. Windows NT 4.0 Ping Response
400-251 dumps Answer: B
QUESTION: 14. In order for your newly written security policy to have any weight, it must be implemented. Which of the following are the three components of a successful Security Policy Implementation in an organization?
A. Policy Monitoring
B. Policy Design
C. Policy Committee
D. Policy Enforcement
E. Policy Documentation
Answer: ABD
QUESTION: 15. Attackers have the ability to use programs that are able to reveal local passwords by placing some kind of a pointer/cursor over the asterisks in a program’s password field. The reason that such tools can uncover passwords in some Operating Systems is because:
A. the passwords are simply masked with asterisks
B. the etc/passwd file is on a FAT32 partition
C. the passwords are decrypted on screen
D. the password text is stored in ASCII format
E. the etc/passwd file is on a FAT16 partition
400-251 pdf Answer: A
QUESTION: 16. To maintain the security of your network you routinely run several checks of the network and computers. Often you use the built-in tools, such as netstat. If you run the following command: netstat -e which of the following will be the result?
A. Displays all connections and listening ports
B. Displays Ethernet statistics
C. Displays addresses and port numbers in numerical form
D. Shows connections for the protocol specified
E. Displays per-protocol statistics
Answer: B
QUESTION: 17. You have become the lead security professional for a mid-sized organization. You are currently studying DNS issues, and configuration options. You come across the concepts of DNS Spoofing, and investigate more. What is DNS Spoofing?
A. DNS Spoofing is when the DNS client submits a false DNS request to the DNS server, and the DNS server responds with correct data.
B. DNS Spoofing is the DNS client submits a DNS request to the DNS server using a bogus IP address, and the DNS server responds to the incorrect host.
C. DNS Spoofing is when a DNS Server responds to an unauthorized DNS client, providing that client with name resolution.
D. DNS Spoofing is when a DNS client is forced to make a DNS query to an imposter DNS server, which send the client to an imposter resource.
E. DNS spoofing is when a DNS server provides name resolution to clients that are located in a different IP subnet than the server itself.
400-251 vce Answer: D
QUESTION: 18. What is a problem with symmetric key cryptography?
A. It is slower than asymmetric key cryptography
B. Secure distribution of the public key
C. There is a lack of encryption protocols that can use symmetric key cryptography
D. Secure distribution of a secret key
E. Symmetric key cryptography is reserved for the NSA
Answer: D
QUESTION: 19. What is the name of the informational page that is relevant to a particular command in Linux?
A. Readme Page
B. Lnx_nfo Page
C. Man Page
D. X_Win Page
E. Cmd_Doc Page
400-251 exam Answer: C
QUESTION: 20. You have just downloaded a new file, called scnpfile.tar.gz. You are going to verify the file prior to un-archiving the file. Which command do you need to type to un-compress the file, prior to un-archiving?
A. tar xvf scnpfile.tar.gz
B. tar -zxvf scnpfile.tar.gz
C. gunzip scnpfile.tar.gz
D. gunzip -xvf scnpfile.tar.gz
E. gunzip -zxvf scnpfile.tar.gz
Answer: C
QUESTION: 21. You are configuring the lines that control access to exported objects on your server running NFS. If you have a directory called /Tech and you wish to export this directory to network 192.168.20.0/24, allowing root access, and the permissions of read and write, which of the following lines will accomplish this?
A. (RW) no_root_squash /Tech 192.168.20.0/24
B. /Tech 192.168.20.0/24 (rw) no_root_squash
C. (RW) no_root_squash 192.168.20.0/24 /Tech
D. (RW)no_root_squash:/Tech 192.168.20.0/24
E. /Tech 192.168.20.0/24(rw) no_root_squash
400-251 dumps Answer: E
QUESTION: 22. You are working on the authentication systems in your network, and are concerned with your legacy systems. In Windows NT 4.0, before Service Pack 4 (SP4), there were only two supported methods of authentication. What were those two methods?
A. NetBIOS
B. LM
C. NTLM
D. NTLMv2
E. Kerberos
Answer: BC
QUESTION: 23. If you encrypt or decrypt files and folders located on a remote computer that has been enabled for remote encryption; the data that is transmitted over the network by this process is not encrypted. In order to keep data encrypted as it is transmitted over the network, which of the following must you do?
A. You must implement EFS.
B. You must implement B2 security for Windows.
C. You must use IPSec.
D. You must use a recovery agent.
E. You must transmit the entire folder, not individual files.
400-251 pdf Answer: C
QUESTION: 24. Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
A. NetBus Scan
B. Trojan Scan
C. Ping Sweep
D. Port Scan
E. Ping Sweep
Answer: D
QUESTION: 25. As per the guidelines in the ISO Security Policy standard, what is the purpose of the section on Business Continuity Planning?
A. The objectives of this section are to maintain appropriate protection of corporate assets and to ensure that information assets receive an appropriate level of protection.
B. The objectives of this section are to provide management direction and support for information security.
C. The objectives of this section are to counteract interruptions to business activities and to critical business processes from the effects of major failures or disasters.
D. The objectives of this section are to avoid breaches of any criminal or civil law, statutory, regulatory or contractual obligations and of any security requirements, and to ensure compliance of systems with organizational security policies and standards.
E. The objectives of this section are to control access to information, to prevent unauthorized access to information systems, to ensure the protection of networked services, and to prevent unauthorized computer access.
400-251 vce 400-251 vce Answer: C
QUESTION: 26. On Monday, during a routine check of a users Windows workstation, you find the following program, called regedit.bat on the users local hard drive: Net localgroup administrators local /all Start regedit.exe Exit What is this program capable of doing on this computer?
A. Nothing, the first line is coded wrong.
B. It will add the administrators to the local group
C. It will add the local user to all local groups
D. It will add the administrators to all local groups
E. It will add the local user to the administrators group
Answer: E
QUESTION: 27. Often times attackers will run scans against the network to identify different network and operating systems, and resources that are available. If an attacker runs scans on the network, and you are logging the connections, which of the following represent the legitimate combination of packets that will be sent between the attacker and target?
A. Attacker PSH-FIN Scan, Target RST-FIN Response
B. Attacker ACK Scan, Target NULL Response
C. Attacker NULL Scan, Target RST Response
D. Attacker SYN Scan, Target NULL Response
E. Attacker FIN Scan, Target RST Response
400-251 exam Answer: CE
QUESTION: 28. You are discussing the design and infrastructure of the Internet with several colleagues when a disagreement begins over the actual function of the NAP in the Internets design. What is the function of a NAP in the physical structure of the Internet?
A. The NAP provides for a layered connection system of ISPs connecting to the backbone.
B. The NAP provides the actual connection point between a local user and the Internet.
C. The NAP provides the physical network with communication channels for the Internet and voice/data applications.
D. The NAP provides a national interconnection of systems, called peering centers, to the NSPs.
E. The NAP provides for a connection point between an ISP and the backbone of the Internet.
Answer: E
QUESTION: 29. When using the 3DES encryption ( C = EK1[DK2[EK1[P]]] ) , what is the function of C?
A. C is the text before encryption
B. C is the first encryption key
C. C is the second encryption key
D. C is the decryption key
E. C is the text after encryption
400-251 dumps Answer: E
QUESTION: 30. Which of the following are symmetric encryption algorithms?
A. MD5
B. RSA
C. Diffie-Hellman
D. 3DES E.
AES Answer: DE
QUESTION: 31
Where does the list of Values (LOV) Job Server store reports when it processes scheduled
List of Value objects?
A. Input File Repository Server B.
Output File Repository Server C.
Repository Manager
D. Central Management Server (CMS) System Database
400-251 pdf Answer: B
QUESTION: 32
What is the recommended value for the Maximum Simultaneous Report parameter of the Desktop Intelligence Report Server?
A. Two greater than the Number of Preloaded Report Jobs value
B. Two less than the Number of Preloaded Report Jobs value
C. The same value set for Number of Preloaded Report Jobs
D. No more than fifty per processor
Answer: A
QUESTION: 33
A user schedules a Crystal Report. What step does the Crystal Reports Job Server take when the Schedule time is reached?
A. Starts a JobServer thread to run the report
B. Spawns a JobServerChild process to run the report
C. Contacts the Crystal Reports Page Server for the location of the report
D. Runs the report immediately by opening the report from the Input File Repository Server (FRS)
400-251 vce Answer: B
QUESTION: 34
Which four servers are involved in processing a scheduled List of Values (LOV) object? (Choose four.)
A. Input File Repository Server
B. Crystal Reports Job Server
C. Output File Repository Server
D. List of values Job Server
E. Central Management Server
Answer: A, C, D, E

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products.Our Cisco 400-251 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
Pass4itsure 400-251 dumps is a milestone in your career. In this competitive world, it is more important than ever. We guarantee that you can pass the exam easily. “CCIE Security Written Exam (v5.0)”, also known as 400-251 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 400-251 dumps exam questions answers are updated (520 Q&As) are verified by experts. The associated certifications of 400-251 dumps is CCIE Security. This certification exam can also help you tap into many new avenues and opportunities. The IT professionals and industrious experts in Pass4itsure make full use of their knowledge and experience to provide the best Cisco CCIE Security https://www.pass4itsure.com/400-251.html dumps CCIE Security practice questions for the candidates.
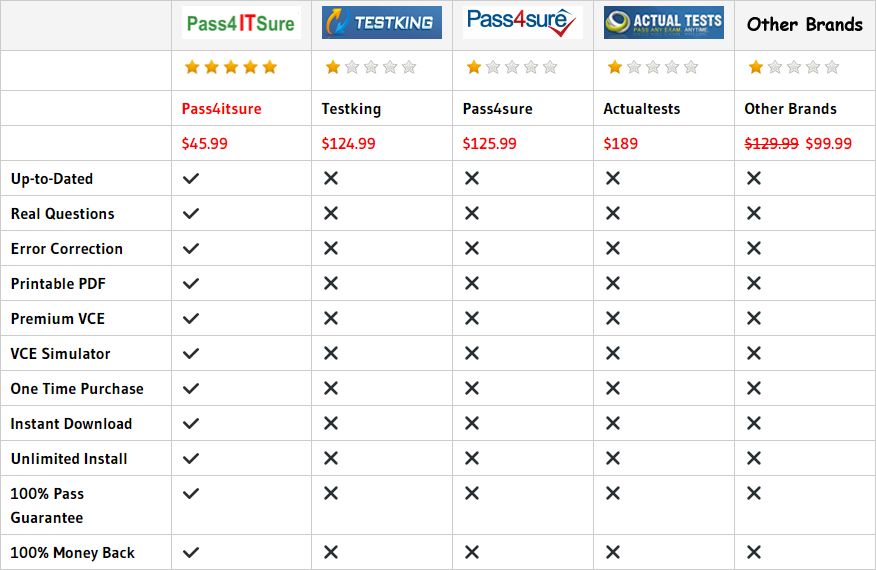
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure Cisco 400-251 Dumps Doc, Buy Cisco 400-251 Dumps Certification Exam Are Based On The Real Exam,We Help You Pass CCIE Security Written Exam (v5.0). Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!
