
Where I can get good quality of exam for Cisco 400-201 dumps? The CCIE Service Provider Written Exam Version 4.1 (400-201 CCIE SP) exam is a 120 minutes (90 – 110 questions) assessment in pass4itsure that is associated with the CCIE Service Provider certification. First-hand Cisco 400-201 dumps exam CCIE SP certification exam questions and answers video study online. “CCIE Service Provider Written Exam Version 4.1” is the exam name of Pass4itsure Cisco 400-201 dumps test which designed to help candidates prepare for and pass the Cisco 400-201 exam. Pass4itsure provides perfect scenario for CCIE Service Provider 400-201 exam prep material with newest https://www.pass4itsure.com/400-201.html dumps questions and 400-201 sample questions which differ from other websites relates to 400-201 new questions and 400-201 dumps.
[Up To Dated -2018 Cisco 400-201 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWV2ZxQlJ2OGxkaXc
[Up To Dated -2018 Cisco 810-403 Dumps From Google Drive]: https://drive.google.com/open?id=0BwxjZr-ZDwwWZ0laMkIyTHdXeWM
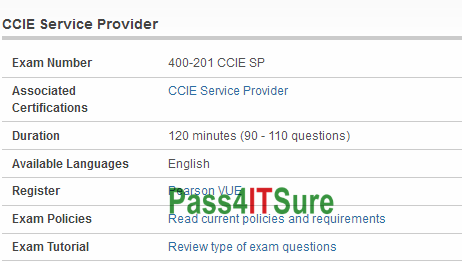
Kill your exam with Cisco 400-201 dumps real questions(7-27)
7. A database is created in one volume group. The data files, meta data files, and journaling logs are all on the same volume group. The database administrator (DBA) has created a remote replica of the volume group over a 100km FCP link. The data base is recovered, tested and shutdown on a remote host. What must the DBA do before restoring the database ?
A. Do nothing
B. Copy the original journaling logs to a safe location, so they can be used to recover the database.
C. Copy the original meta data files to a safe location, so they can be used to recover the database.
D. Copy the original journaling logs and meta data files to a safe location, so they can be used to recover the database.
400-201 exam Answer: B
8. A production cluster is attached to redundant disk fabrics and a tape fabric. Each fabric is contained within a single switch. Each cluster member has access to 12 TBs of RAID 1 production storage and 12 TBs of RAID 0 local replica accessed through eight HBAs single initiator zoned to sixteen storage ports to one storage array. The tape fabric includes one (1) connection to each server and direct connections to ten LTO II tape drives. The standby cluster member performs multi-threaded backups using the local replica. All HBAs and ports are 200 MB. If the recovery time is equal to backup time, where is the bottleneck?
A. tape HBA
B. disk HBAs
C. tape drives
D. array contention
Answer: A
9. A server is experiencing performance problems. An application is being migrated to a new server. In a controlled environment, how would you migrate the application with the least amount of downtime?
A. Shutdown the application, copy the data to the new server over the network, start the application on the new server.
B. Shutdown the application, change zoning and LUN masking information, start the application on the new server.
C. Create a local replica, change zoning and LUN masking information, stop the application, start the application on the new server.
D. Apply the zoning and LUN masking information for the new server, stop the application, start the application on the new server, remove the zoning and LUN masking information on the old server.
400-201 dumps Answer: D
10. A Solaris administrator responsible for backups is informed that the restore of data from the backup appeared to be corrupt. The backups had appeared successful, but the database administrator claims the data that was restored is invalid. Where can the administrator check to see if errors occurred during the backup or recovery process?
A. /etc/syslog
B. event viewer
C. /var/adm/messages
D. /usr/sbin/errorlog.log
Answer: C
11. A customer with eight SAN attached hosts has a storage array with only ten disk drives. The customer wishes to protect their data by using a RAID 1 protection scheme. Each server has a need to see three separate volumes for their final configuration. What must be configured on the array to meet their storage allocation needs?
A. multiple scsi targets to each mirror volume
B. separate logical units for each server volume
C. separate virtual paths for each mirror volume
D. multiple COW snapshots for each server volume
400-201 pdf Answer: B
12. A customer wants to deploy a disaster recovery site 30 km away from the primary data center using a Fibre Channel link. What is the key factor for maximizing performance of the link?
A. cable type
B. link control
C. adequate buffer credits
D. Fibre Channel class of service
Answer: C
13. When adding a new Fibre Channel switch to a fabric, which step should you take, before connection, to maintain security of the production network?
A. disable all ports
B. change default password
C. disable E_PORT functionality
D. upgrade firmware using an isolated fabric
400-201 vce Answer: B
14. Where would you find the N_Port in a fabric?
A. on an inter-switch link
B. on the Fibre Channel HBA
C. on the Fibre Channel switch D. on the Fibre Channel loop device
Answer: B
15. What are two advantages of WWN (soft) zoning over port (hard) zoning? (Choose two.)
A. Switch ports can be grouped together to form a zone.
B. A device can be moved to another switch in the same Fabric without reconfiguring zoning.
C. A device can be moved to another port on a switch following switch port failure without reconfiguring zoning.
D. A Fibre Channel tape drive can be replaced with another unit that has a different WWN without reconfiguring zoning.
400-201 exam Answer: BC
16. Given the limitation of short wave fiber, which statement is true?
A. Short wave fiber can be used for MAN connections.
B. Short wave fiber can be used for WAN connections.
C. Short wave fiber connections are good up to 10 km.
D. Short wave fiber connections are used for localized SANs.
Answer: D
17. You have an existing RAID system with 16 drives. The existing system was used to provide volumes to six Windows systems on 2-gigabit links. You decide to add another 16 drive tray to double the number of your raw hard drives in order to support five new UNIX servers. The average server throughput is 20 MB/sec. The RAID head is dual ported and configured active-passive. What may occur?
A. The zoning on the switch will control the traffic flow to the RAID.
B. The added demands on the RAID system will saturate the active RAID port.
C. The RAID system will notice the extra requests and go active-active to support the load.
D. The Windows systems will receive precedence as they were registered first on the RAID.
400-201 dumps Answer: B
18. A fibre switch fails. A replacement switch has been delivered. Before plugging the replacement switch into the SAN, which two actions should be taken? (Choose two.)
A. Delete fabric records of the old switch.
B. Add the new switch to the current zone configuration.
C. Clear all zoning information on the replacement switch.
D. Change the Domain ID of the replacement switch to the Domain ID of the old switch.
Answer: CD
19. When planning to deploy a Fibre Channel infrastructure where data rates are expected to exceed 25MB/sec what is the preferred medium for local cabling requirements up to 500 meters?
A. 9/125 single-mode optical cables
B. 50/125 multi-mode optical cables
C. 62.5/125 multi-mode optical cables
D. 62.5/125 multi-mode copper cables
400-201 pdf Answer: B
20. What are two advantages of over-subscription? (Choose two.)
A. saves on ISL links
B. decreases host I/O latency
C. increases individual host throughput
D. increases the number of hosts that can use the ISL
Answer: AD
21. You have just become the senior security professional in your office. After you have taken a complete inventory of the network and resources, you begin to work on planning for a successful security implementation in the network. You are aware of the many tools provided for securing Windows 2003 machines in your network. What is the function of Secedit.exe?
A. This tool is used to set the NTFS security permissions on objects in the domain.
B. This tool is used to create an initial security database for the domain.
C. This tool is used to analyze a large number of computers in a domain-based infrastructure.
D. This tool provides an analysis of the local system NTFS security.
E. This tool provides a single point of management where security options can be applied to a local computer or can be imported to a GPO.
400-201 vce Answer: C
22. To increase the security of your network and systems, it has been decided that EFS will be implemented in the appropriate situations. Two users are working on a common file, and often email this file back and forth between each other. Is this a situation where the use of EFS will create effective security, and why (or why not)?
A. No, the security will remain the same since both users will share the same key for encryption.
B. Yes, since the file will be using two keys for encryption the security will increase.
C. No, the security will remain the same since both users will share the same key for decryption.
D. Yes, since the file will be using two keys for decryption the security will increase.
E. No, EFS cannot be used for files that are shared between users.
Answer: E
23. Recently, you have seen an increase in intrusion attempts and in network traffic. You decide to use Snort to run a packet capture and analyze the traffic that is present. Looking at the example, what type of traffic did Snort capture in this log file?
A. Windows 2000 Ping Request
B. Windows NT 4.0 Ping Request
C. Linux Ping Request
D. Linux Ping Response
E. Windows NT 4.0 Ping Response
400-201 pdf Answer: B
24. In order for your newly written security policy to have any weight, it must be implemented. Which of the following are the three components of a successful Security Policy Implementation in an organization?
A. Policy Monitoring
B. Policy Design
C. Policy Committee
D. Policy Enforcement
E. Policy Documentation
Answer: ABD
25. Attackers have the ability to use programs that are able to reveal local passwords by placing some kind of a pointer/cursor over the asterisks in a program’s password field. The reason that such tools can uncover passwords in some Operating Systems is because:
A. the passwords are simply masked with asterisks
B. the etc/passwd file is on a FAT32 partition
C. the passwords are decrypted on screen
D. the password text is stored in ASCII format
E. the etc/passwd file is on a FAT16 partition
400-201 vce Answer: A
26. To maintain the security of your network you routinely run several checks of the network and computers. Often you use the built-in tools, such as netstat. If you run the following command: netstat -e which of the following will be the result?
A. Displays all connections and listening ports
B. Displays Ethernet statistics
C. Displays addresses and port numbers in numerical form
D. Shows connections for the protocol specified
E. Displays per-protocol statistics
Answer: B
27. You have become the lead security professional for a mid-sized organization. You are currently studying DNS issues, and configuration options. You come across the concepts of DNS Spoofing, and investigate more. What is DNS Spoofing?
A. DNS Spoofing is when the DNS client submits a false DNS request to the DNS server, and the DNS server responds with correct data.
B. DNS Spoofing is the DNS client submits a DNS request to the DNS server using a bogus IP address, and the DNS server responds to the incorrect host.
C. DNS Spoofing is when a DNS Server responds to an unauthorized DNS client, providing that client with name resolution.
D. DNS Spoofing is when a DNS client is forced to make a DNS query to an imposter DNS server, which send the client to an imposter resource.
E. DNS spoofing is when a DNS server provides name resolution to clients that are located in a different IP subnet than the server itself.
400-201 exam Answer: D

See What Our Customers Are Saying:
We at Pass4itsure are committed to our customer’s success. There are 50,000+ customers who used this preparation material for the preparation of various certification exams and this number of customers is enough for new candidates to trust in these products.Our Cisco 400-201 dumps are created with utmost care and professionalism. We utilize the experience and knowledge of a team of industry professionals from leading organizations all over the world.
There can be a lot of reasons for doing CCIE Service Provider certifications and people show their interest in the CCIE SP 400-201 questions and searching for accurate CCIE SP 400-201 answers with 400-201 dumps, however its easy to pass Cisco 400-201 exam with the help of Pass4itsure 400-201 training material which comes with CCIE SP 400-201 test pdf dumps, 400-201 vce and 400-201 questions. “CCIE Service Provider Written Exam Version 4.1”, also known as 400-201 exam, is a Cisco certification which covers all the knowledge points of the real Cisco exam. Pass4itsure Cisco 400-201 dumps exam questions answers are updated (618 Q&As) are verified by experts. The associated certifications of 400-201 dumps is CCIE Service Provider. Pass4itsure provides you latest CCIE SP https://www.pass4itsure.com/400-201.html dumps test questions and answers with up to date 400-201 sample questions verified by Cisco certified experts.
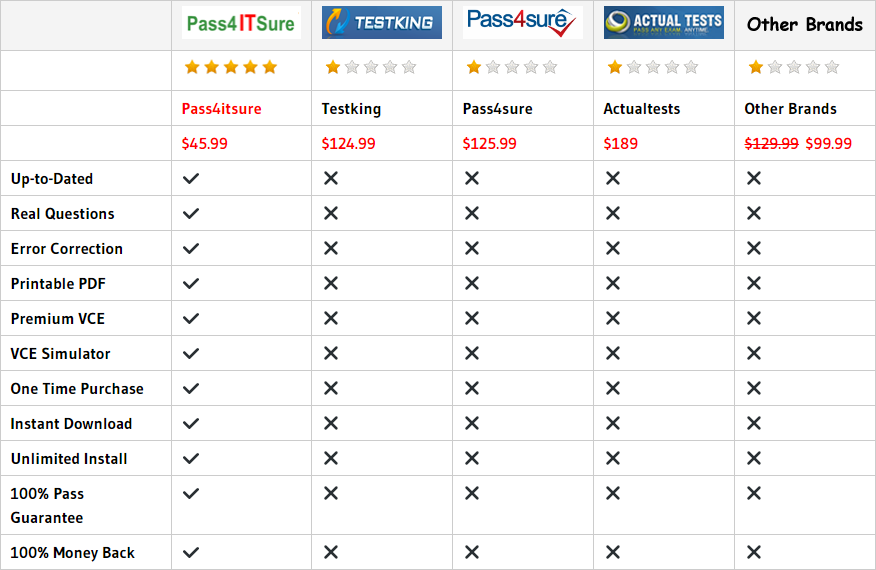
Compared with other brands, Pass4itsure has up to dated exam information, affordable price, instant exam PDF files downloaded, error correction, unlimited install,etc. Such as Pass4itsure Cisco 400-201 Dumps Certification, First-hand Cisco 400-201 Dumps Online, We Help You Pass CCIE Service Provider Written Exam Version 4.1. Simple and Easy! To take advantage of the guarantee, simply contact Customer Support, requesting the exam you would like to claim. Pass4itsure guarantee insures your success otherwise get your MONEYBACK!
